Scan multimedia files for data that puts your company at risk.
AI-powered detection, built to prevent media-driven breaches.
Real threats,
found in real files.
We've scanned millions of images, videos, and audio files — and uncovered thousands of hidden risks companies constantly overlook.
MEDIAMINER ANALYSIS
That's thousands of multimedia files exposing companies every day.
The hidden security risk in everyday media
Countless times a day, people unknowingly share media files that reveal sensitive data. It moves across cloud, chat, social platforms and internal networks undetected by traditional tools. We detect what others miss — and turn overlooked media into actionable insight.

THE SUITE
From discovery to defense.
Go deeper than detection. We help your company map how threats escalate, simulate real-world attacks and take action.

Defend by detecting
sensitive data in media.
Continuously scan corporate networks, public sources and even supplier activity — and identify media that exposes sensitive company information. We turn the noise into action, so you can focus on defending — not digging.
CYBER THREAT INTELLIGENCE
Find threats where they begin.
Finding risks starts with knowing where they live. Cover every surface — from internal to external channels — with continuous media-focused threat monitoring.

NIS 2 Compliance
Built to meet the EU NIS 2 Directive's stringent cybersecurity and reporting requirements.
Internal network
Scan files across your infrastructure to detect images, videos, or audio that could leak credentials, documents, or workspace visuals — ensuring GDPR and compliance readiness.
Internal StoragePublic relations
Pre-scan visual and audio content before release to prevent accidental disclosure of sensitive information in press, blogs, or social campaigns.
Internal StorageSupply chain
Continuously monitor vendor, agency, and affiliate media to flag files revealing sensitive project details, tools, or internal locations.
Social Media PlatformBreached accounts
Continuously scan media from employees or connected accounts to detect leaked credentials or exposed datasets.
Social Media PlatformOpen search
Continuously monitor social platforms for organization-related keywords to find sensitive information, critical mentions, or exposed corporate data.
Social Media PlatformMicrosoft 365 integration
Analyze media shared within Microsoft 365 to detect content that may contain sensitive data or compromising information.
Internal Storage
NIS 2 Compliance
Built to meet the EU NIS 2 Directive's stringent cybersecurity and reporting requirements.
Our top use cases

Credential exposure via workstation photo
A senior executive’s motivational post unintentionally exposed critical system credentials, creating a direct path to network compromise.
In a show of dedication, a General Manager shared a photo of his workstation on social media, celebrating late-night work. On the monitor, however, a file titled “password server nuovo.docx” was visible. Automated analysis revealed that the document contained admin credentials for production servers, firewall access, and VPN accounts.
For an attacker, this image alone would have been enough to gain privileged access to the company’s infrastructure and move laterally across systems.
MediaMiner flagged the exposure in real time, prompting immediate removal of the post, credential revocation, and a password rotation. The incident also sparked an internal awareness campaign, underscoring how even well-intentioned posts can pose serious risks.

Social engineering via social media post
A seemingly harmless photo of a company printer shared online opened the door to one of the most advanced social engineering attacks.
A well-meaning employee posted a picture of a printer on social media, inadvertently exposing its serial number, product number, PIN, and warranty QR code. These details were enough for an attacker to impersonate an HP technician.
Claiming a warranty issue, the attacker gained physical access to the company premises. During the intervention, they installed a backdoor into the IT infrastructure, securing remote and persistent access.
MediaMiner automatically flags images of this kind as high-risk, helping clients detect similar exposures early and strengthen policies on how technical details are shared in images.
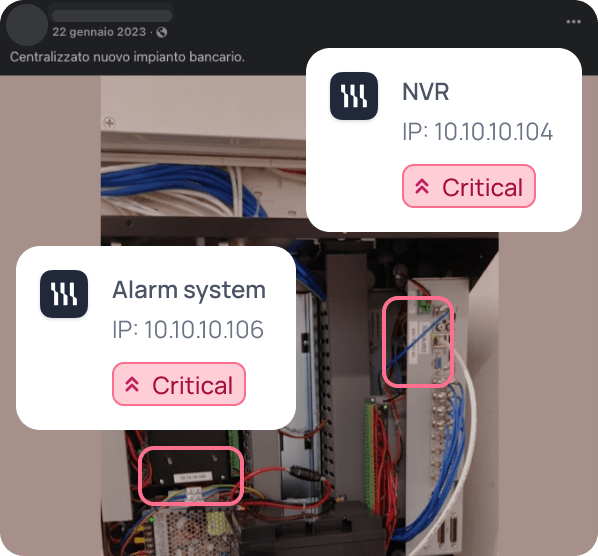
Supply chain risk via vendor installation post
A supplier’s post revealed sensitive details of a bank’s infrastructure, showing how third-party mistakes can expose even the most secure organizations.
During a Red Team engagement for a global bank, MediaMiner detected images published by a physical security vendor on their website and social channels. The photos, taken during alarm system and NVR installations at bank branches, inadvertently exposed IP addresses and detailed control panel configurations.
What seemed like harmless marketing material in fact provided attackers with a technical map to bypass physical and network defenses. This incident highlighted how even well-defended organizations remain vulnerable through their suppliers.
By flagging the exposure, MediaMiner enabled the bank to remove the content, expand audits across its supply chain, and enforce stricter rules on what images partners are allowed to publish.
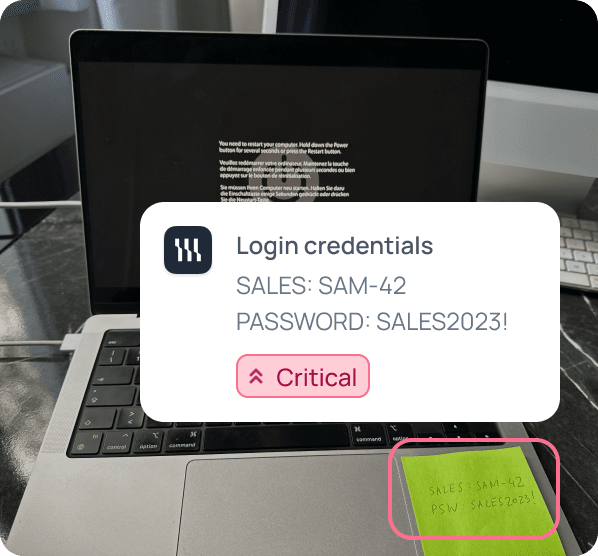
Credential exposure via helpdesk screen photo
An innocent helpdesk request turned into a major security risk when sensitive credentials were captured in a simple photo of the screen.
A retail group employee reported a terminal error by emailing a photo of their laptop. The image unintentionally exposed a sticky note with CRM login details and domain credentials. Archived in ticket logs and backups, the data became a hidden treasure for potential attackers.
In an assume-breach scenario, attackers could retrieve the image, use the credentials for lateral movement, escalate privileges, and compromise critical business systems.
With proactive detection, organizations can stop these “invisible” leaks before they escalate into business continuity and compliance crises.

A senior executive’s motivational post unintentionally exposed critical system credentials, creating a direct path to network compromise.
In a show of dedication, a General Manager shared a photo of his workstation on social media, celebrating late-night work. On the monitor, however, a file titled “password server nuovo.docx” was visible. Automated analysis revealed that the document contained admin credentials for production servers, firewall access, and VPN accounts.
For an attacker, this image alone would have been enough to gain privileged access to the company’s infrastructure and move laterally across systems.
MediaMiner flagged the exposure in real time, prompting immediate removal of the post, credential revocation, and a password rotation. The incident also sparked an internal awareness campaign, underscoring how even well-intentioned posts can pose serious risks.

A seemingly harmless photo of a company printer shared online opened the door to one of the most advanced social engineering attacks.
A well-meaning employee posted a picture of a printer on social media, inadvertently exposing its serial number, product number, PIN, and warranty QR code. These details were enough for an attacker to impersonate an HP technician.
Claiming a warranty issue, the attacker gained physical access to the company premises. During the intervention, they installed a backdoor into the IT infrastructure, securing remote and persistent access.
MediaMiner automatically flags images of this kind as high-risk, helping clients detect similar exposures early and strengthen policies on how technical details are shared in images.
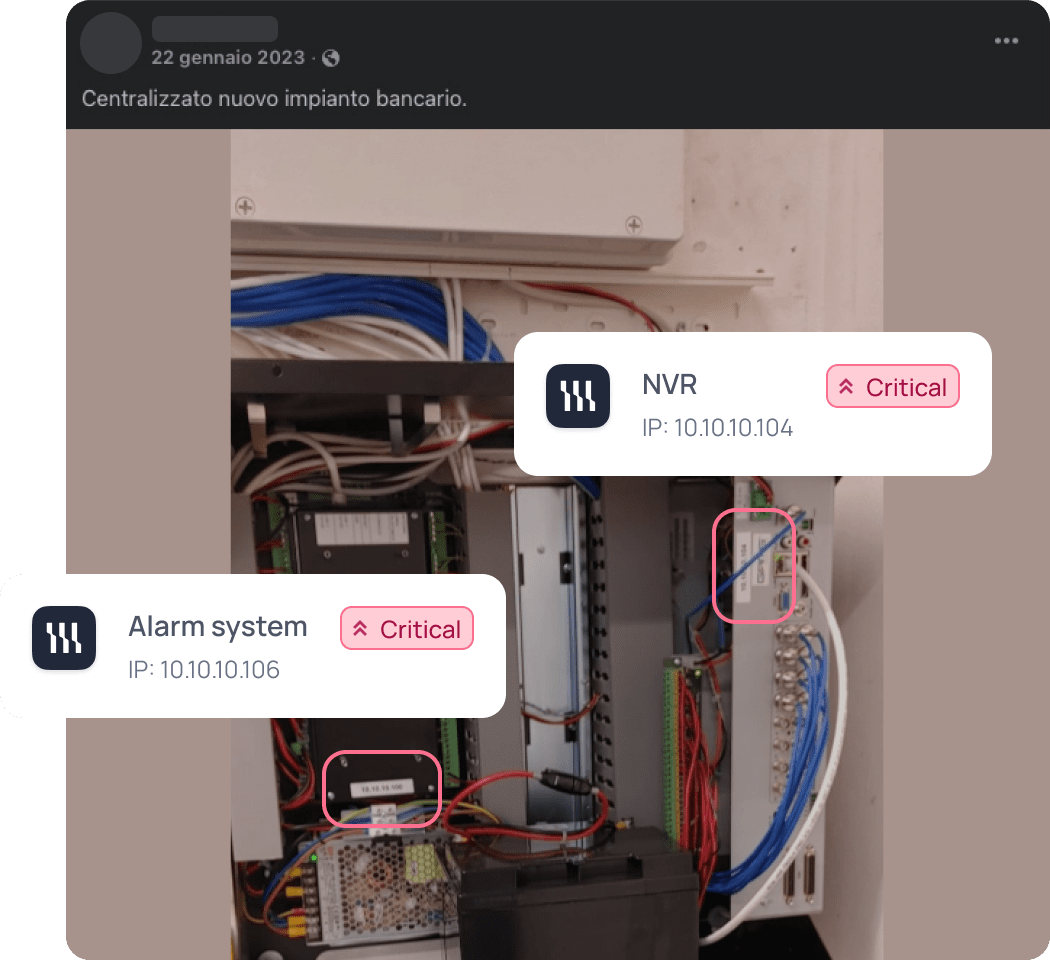
A supplier’s post revealed sensitive details of a bank’s infrastructure, showing how third-party mistakes can expose even the most secure organizations.
During a Red Team engagement for a global bank, MediaMiner detected images published by a physical security vendor on their website and social channels. The photos, taken during alarm system and NVR installations at bank branches, inadvertently exposed IP addresses and detailed control panel configurations.
What seemed like harmless marketing material in fact provided attackers with a technical map to bypass physical and network defenses. This incident highlighted how even well-defended organizations remain vulnerable through their suppliers.
By flagging the exposure, MediaMiner enabled the bank to remove the content, expand audits across its supply chain, and enforce stricter rules on what images partners are allowed to publish.
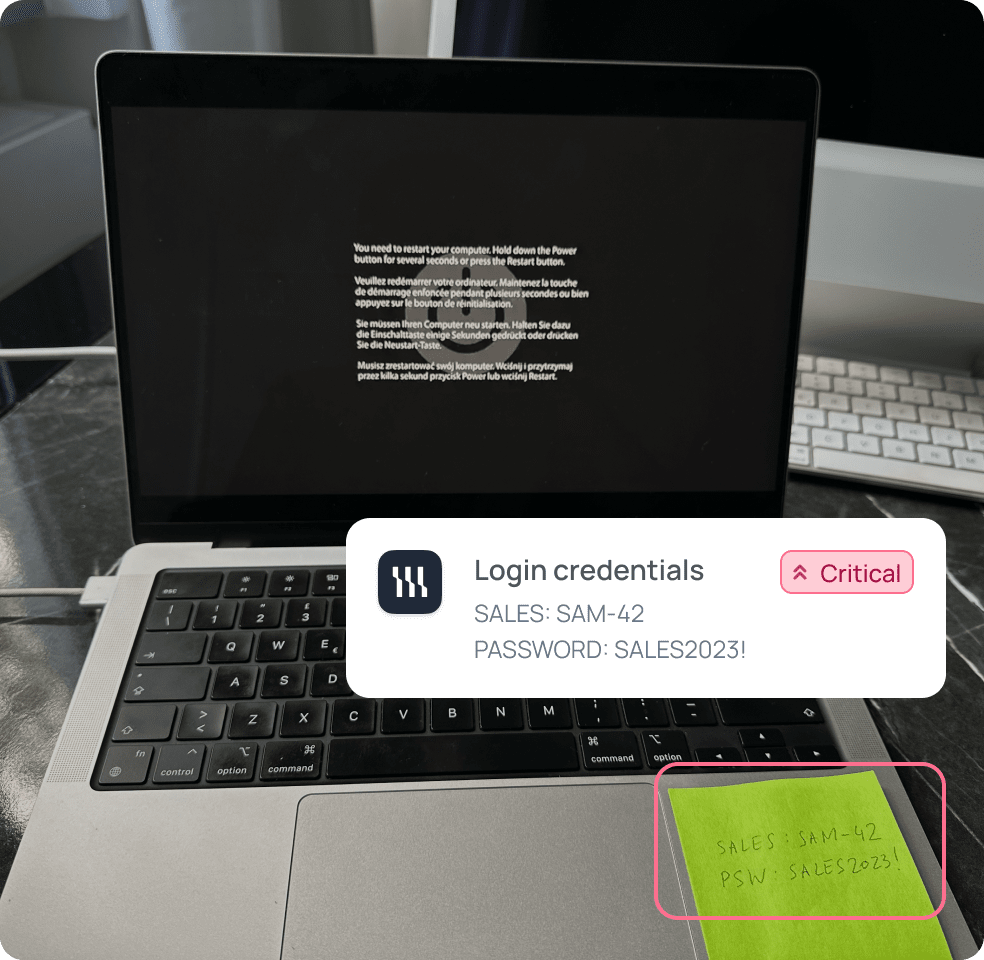
An innocent helpdesk request turned into a major security risk when sensitive credentials were captured in a simple photo of the screen.
A retail group employee reported a terminal error by emailing a photo of their laptop. The image unintentionally exposed a sticky note with CRM login details and domain credentials. Archived in ticket logs and backups, the data became a hidden treasure for potential attackers.
In an assume-breach scenario, attackers could retrieve the image, use the credentials for lateral movement, escalate privileges, and compromise critical business systems.
With proactive detection, organizations can stop these “invisible” leaks before they escalate into business continuity and compliance crises.
View, prioritize, and resolve threats from
one collaborative dashboard
PRIORITIZATION
Threat severity
Each threat is classified by severity — so your team knows what to address first.

THREAT MANAGEMENT
Incident workflow
Organize threats by status — validate, resolve or dismiss. Keep every case under control.

COLLABORATION
Work better, together
Assign threats, leave comments, and mention teammates — all in one shared view.

THREAT ANALYTICS
From data to decisions
Visualize exposure trends, source breakdowns, and risk levels.

Adaptive AI-powered media analysis built
for smart detection


We help you simulate attack before it's real, using media found.
We go beyond detection with AI- and human-driven testing. Using found media, we simulate realistic attacks — from vulnerability scans to full red teaming — showing exactly how exposed your organization is, and how to fix it before attackers strike.
OFFENSIVE SECURITY
Built by experts who think like attackers.
The best defense is a strategic offense. We simulate real attacks to expose your vulnerabilities — so you can fix them before the real threat arrives.
Vulnerability Assessment
AI-drivenMap media risks across your environment. Scan your internal and external network to detect sensitive media that expose your organization. Each finding is classified, tied to a realistic attack path, and comes with clear remediation steps.
Penetration Testing
AI-drivenSee how far an attacker could go. Automatically simulate privilege escalation using media-based findings from the Vulnerability Assessment. Measure tangible proof of how far an attack could escalate.
Penetration Testing
Human-drivenLet ethical hackers test your real attack surface. A specialized team leverages the findings to exploit vulnerable entry points. Using advanced manual techniques, we demonstrate how media can be used to pivot into your systems.
Red Teaming
Human-drivenSimulate a full-scale attack — tailored to your business. Define a critical asset (the "flag"), and let our red team replicate the behavior of persistent threat actors.

Explore the power of AI threat detection.
Take a tour: explore the platform and scan media files to detect potential threats.
Start free trial





